Translated by Anette Eklund
Some groups use technology failures to do business, by exploiting its vulnerabilities for specific purposes. Such was the case of the WannaCry computer attack, which hijacks computers and devices to later demand money.
The following is an account of the botnet that was behind the computer attack on the communications outlet Másde131 during 2016, in the context of a series of temporarily close attacks -and with similar techniques- carried out against the sites of Rompeviento TV and Radio Zapote.
In the second week of June 2016, the infrastructure that makes the www.masde131.com site work detected that the database in charge of storing the contents had suffered from an unusual modification, which was later identified as being made by an intruder. In response to this, the newsroom immediately decided to temporarily disable the website until it had a diagnosis of the level of security compromise, in order to protect the browsing of readers and editors.
The analysis process began with the preservation of the system logs and their configurations, to later extract them. These records allow reconstructing the different phases, techniques involved and their development to determine the level of commitment; in other words, the levels of control that the attacker managed to gain either partially or completely.
The analysis process began with the preservation of the system logs and their configurations, to later extract them. These records allow reconstructing the different phases, techniques involved and their development to determine the level of commitment; in other words, the levels of control that the attacker managed to gain either partially or completely.
Through integrity tests of the aforementioned files, the analyzes identified the following:
- The attacker managed to gain control of a user with privileges to write articles, not publish them, this was achieved through continuous login attempts with random passwords.
- With this access, he repeatedly tried to modify the latest entries to place HTML tags that would allow ads to be inserted.
Once the level of commitment was determined, a recovery plan from the backups was executed, taking considerations and security measures; among them, a special containment system against attacks developed by Deflect of the Equalit.ie organization. Subsequently, the investigation continued to learn more about the profile of the attack and document the infrastructure involved.
Some of the requirements to materialize an attack like the one discussed here are bandwidth and processing capabilities to make requests continuously, recurrently, and automatically.
There are several documented ways on how to obtain machines with bandwidth and processing to carry out attacks, one of them is renting them or paying for the infrastructure directly; another is through remote control of other people’s computers or devices, using a part of their available resources to have a set of computers… Which is also known as a type of botnet.
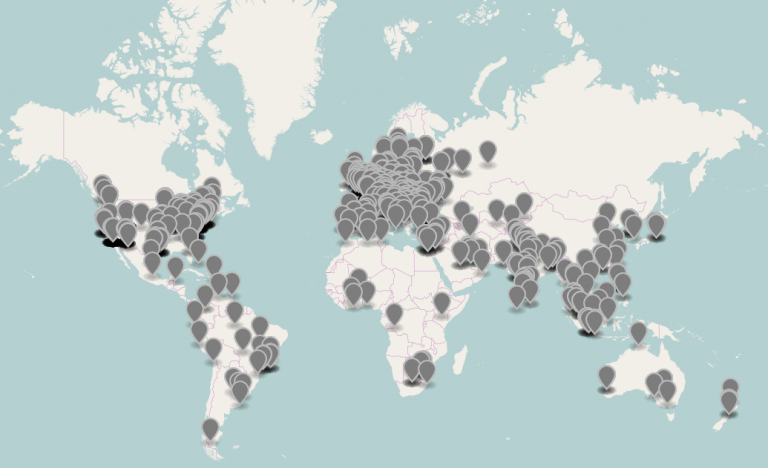
The botnet that attacked Másde131 had at least 25,000 IP addresses, of which we took a sample of 1,200 to position it on a map so that the geographical address corresponded to the associated record. This means that each point on the map is associated with a record of those addresses, although this does not necessarily imply that the connection comes from the indicated points.
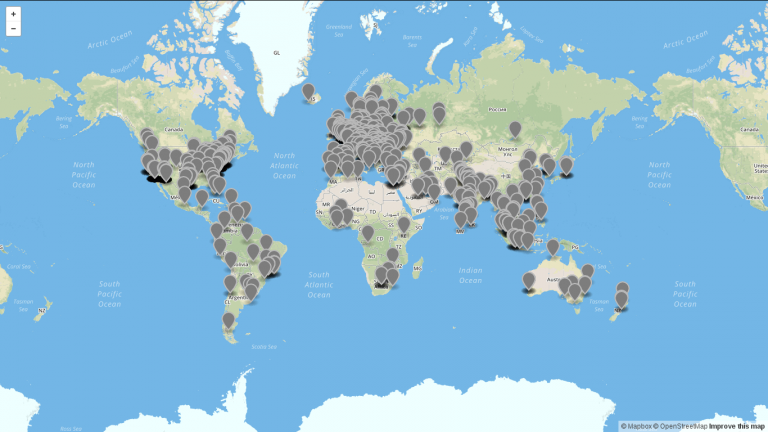
A matching analysis by technique and infrastructure, which even shares several of the IP addresses with this case, was published by the company WordFence earlier this year. WordFence’s report notes that once the botnet gains control of a website, it seeks to place Google ad banners in the header files of the compromised site as a way to monetize the attack.
Exploiting a weak password vulnerability on the made131.com site allowed temporary control over its database to be gained. However, what allowed the attack to be carried out is an exponential problem in which all of us who use technology, as well as manufacturers and service providers, are involved; since our relationship with technology creates a space in which groups can exist that explore business models from the exploitation of technological vulnerabilities to generate profits.
Published in Enjambre Digital, August 3rd, 2017